Usefulness of hashing algorithm in organizations
We use mobiles or any other devices to perform several tasks. Using such modernized devices, we can send text or picture messages to someone. We can also call someone or browse information using wi-fi. Many people use such devices to perform some routine tasks of the business. But these devices are sometimes exposed to security threats. Many people are browsing information using these devices and information can be passed incessantly to unknown parties. So, to prevent such malicious attacks, these devices should always be protected. The data should be secured so that it is not subjected to any thefts or leaks. Sometimes, the problem of the device is not diagnosed properly. So, the experts use different techniques to diagnose the problem. Hashing algorithm is one of the best methods to detect and authenticate data. It is used to secure documents using hashes.
Uses of algorithms in securing data
Hash is a function used to secure the document when the scan is complete. It is a form of approval seal to authenticate data. The data is compared with the original data. It is a numerical algorithm to locate data of various size or type. It is a two-way function used to covert data array to a string of a certain length. It is a function that is used to take any input and convert it into a message using a table. It is a mathematical function that is used to make the data readable.
The data management is used in an organization for various uses.
It is used to store passwords and used to apply digital signatures. It is also used to manage the documents and files. It is also used to secure data scrambling to prevent data leakage.
Why should you protect the data from the devices and the strategies undertaken by the experts?
The hackers are able to easily invade data from the devices. So, merely adding passcodes or usernames cannot prevent data leakage. So, the experts are using some modern methods to prevent leakage of sensitive data. They are using such advanced programs that the hackers are not able to derive information. The malicious attackers are able to open any device or any application easily understanding the pattern of the password or secret codes. So, the experts are using such programs that the malicious attackers may open the application but are not able to derive information from the program. The information is converted into complicated syntaxes, labels, or any other symbols. The attackers cannot understand the ways to operate any software or application. They also reassign some meaningless labels or symbols to any information. For e.g. For credit card number, they may use some symbol or assign some vague name such as icon. So, the attacker is literally bored to acquire information. The experts are using advanced methods for securing the data and preventing data leakage. The data can be easily leaked from the devices as they are using internet to share information. In the process of sharing information, the data is easily invaded.
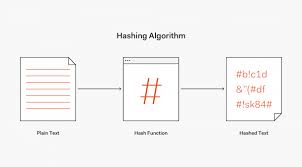
What is hash algorithm?
Hashing algorithm is also such method of preventing any malicious attack on your system preventing the leakage of information. Some of
the fine examples of hashing algorithm are LANMAN, MD5, SHA-2, etc. the most commonly used algorithm is MD5.A hash is a function used to convert data into hashes. So, the data is made so complicated for the readers to understand.
It accepts input and converted the data into a string of certain length or value. The hash can be used for assigning a password and also for larger files with abundant text. The hash is usually a short code even when derived from large data. Even if the user processes large data, it is converted into a string of certain value. Hence it is a fast and efficient means of securing data used to secure several documents. If the hash is larger, the inversion becomes even difficult. The output delivered is limited, but the input can be unlimited. Hashes are also used as fingerprints for original data.
It is an application for converting input data into a string of certain length and value. It is used to accept an input and convert the message in the form of hashes or hashing tables.
It is a procedure of calculating hash value and protecting against interference. It is a function that accepts the information or data as an input and convert it into a certain value of a table. The data converted into strings is in the form of a table. It is used to distribute data across the hash values. It consists of different hash values for similar strings. So, Appsealing provides hashing algorithm services to the organizations or customers to protect the data.
Following are the characteristics of the hashing function:
Should be quickly converted: It is a function used for real-life applications for efficient computation. The message should be converted quickly into a hash value. The computation of the message should be quicker. Only if the speed of conversion is quick, then it can protect the data. Otherwise, if the process of conversion is slower, then the malicious attacker may be able to read or understand the message.
Should be converted into output of desired length: Even if you input the message into the function many times, it should produce the same output. Even if the data that is sent for processing is lengthier, the strings should be produced of the desired length.
The malicious attackers should not be able to trace
The hackers should not be able to perform the function of reverse engineering or should not be able to retrace from the output. The output should not give an idea to the reader about the content. As it is a one-way function, it can be easily reversed. So, the experts should undertake steps to produce strings that are complicated to prevent leakage of sensitive data.
Some of the popular form of algorithms are scrypt, secure hash algorithm, MD5, RSA etc.
Appsealing is providing the best services of securing data to the customers.




